Scan2x Security Advisory
ID: S2X‐SA‐2025‐001
Date: May 16, 2025
Executive Summary
Critical security vulnerabilities have been identified in a third-party Scan2x bundled dependency (Erlang/OTP). Successful exploitation could allow remote code execution, denial of service, or unauthorised data access. All customers must upgrade to Scan2x v3.0.2.1 immediately.
Affected Versions
- Scan2x v3.0.0 through v3.0.2
- Bundled components:
- Erlang/OTP 27.1 (
otp_win64_27.1.exe)
- Erlang/OTP 27.1 (
Vulnerability Details
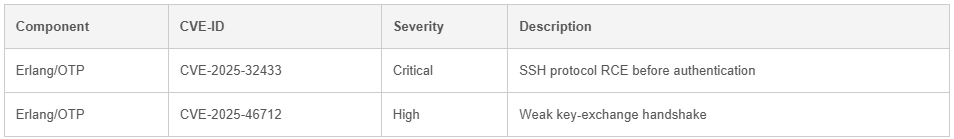
Impact
- Remote Code Execution (CVE-2025-32433): Unauthenticated attackers may execute arbitrary code on the Scan2x host via the SSH server, resulting in system compromise.
- Handshake Manipulation (CVE-2025-46712): A man-in-the-middle could inject or alter messages during the SSH key-exchange, leading to session hijacking, credential interception, or traffic tampering.
Recommended Action
For On-Premise implementations, and all Windows versions of Scan2x:
- Download and install Scan2x v3.0.2.1, by clicking the Check for Updates button at bottom left of the Scan2x Windows application.
- Verify in the “About” dialog that version reads 3.0.2.1.
For Cloud versions: Our hosted Scan2x service is not affected by these vulnerabilities. No further action is required on your part—your environment is protected.
Workarounds
If you cannot upgrade immediately:
- Block port 22/TCP
- In the update to 3.0.2.1, the Scan2x software will uninstall the affected version of Erlang before installing the new updated version. In very isolated cases and under specific scenarios, we have found that the Erlang uninstall function does not complete due to permissions issues.
To ensure that we handle the vulnerability comprehensively, Scan2x is designed to stop the update in the event that the uninstall fails, and we recommend that you follow this documentation to manually uninstall the vulnerability and install the secure version.
The Erlang component is not a Scan2x developed component, however it is referenced by Scan2x – if you are unable to complete these steps, we invite you to email us for support on the contact email below and we will help you with this step. In the vast majority of cases, Scan2x will be able to verify the complete uninstall of the affected component and will continue the update process automatically.
Please note that this update also be installed on clients running the beta version.
Contact & Support
If you have questions or need assistance, please contact Scan2x Support:
-
- Email: support@avantech.com.mt
- Phone: +356 21488800
- Support Portal: https://tasks.avantech.com.mt/
Revision History
15-05-2025: Initial publication